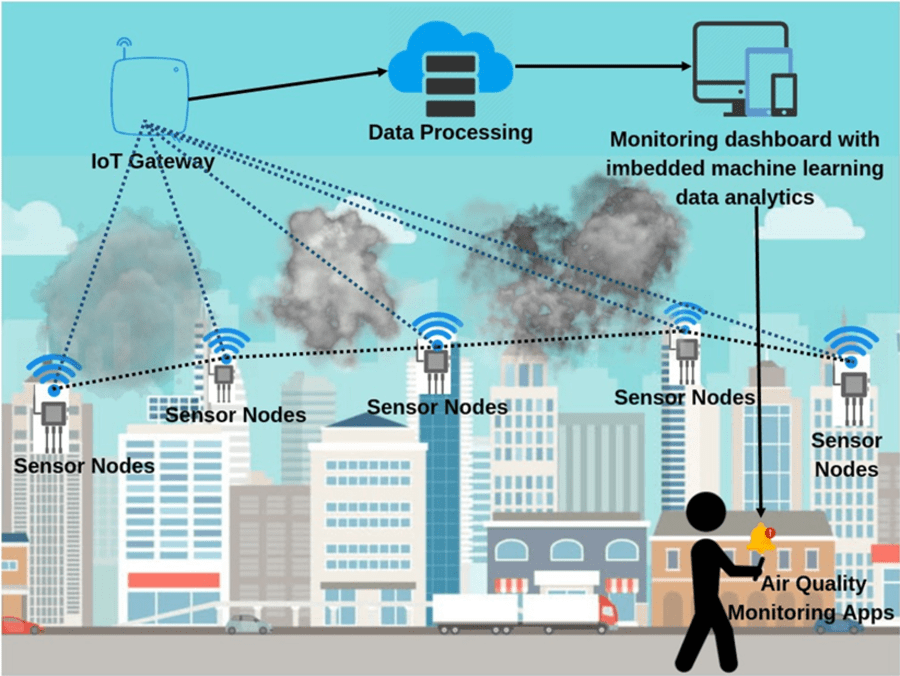
Mastering Control IoT Behind Firewall: Your Ultimate Guide
Hey there, tech enthusiasts! If you're diving into the world of IoT and wondering how to control IoT devices behind a firewall, you're in the right place. Firewalls are like digital bouncers at a club—they decide who gets in and who doesn’t. But what happens when you want your IoT devices to communicate freely while still staying secure? That’s where controlling IoT behind a firewall becomes crucial. Let’s break it down!
Picture this: you’ve got a smart home setup with lights, thermostats, and cameras all connected to the internet. But wait—what if your firewall is blocking these devices from talking to each other or connecting to external servers? Frustrating, right? That’s why understanding how to control IoT behind a firewall is essential for both security and functionality.
This guide isn’t just another tech jargon-filled article. We’ll keep it real, simple, and packed with actionable tips so you can take charge of your IoT network without compromising on security. Let’s get started!
Read also:Edwin Schlossberg Net Worth A Closer Look At The Visionary Mind Behind The Numbers
Table of Contents
- What is IoT Anyway?
- Firewall Basics: Why They Matter
- Challenges of Controlling IoT Behind Firewalls
- Solutions for Managing IoT Devices Securely
- Top Tools to Control IoT Behind Firewalls
- Best Practices for IoT Security
- Designing a Robust Network Architecture
- Protecting Your Data in IoT Networks
- Real-World Examples of IoT Behind Firewalls
- Future Trends in IoT and Firewall Management
What is IoT Anyway?
IoT, or the Internet of Things, is basically the network of physical objects—devices, vehicles, appliances, etc.—that are embedded with sensors, software, and connectivity. Think about your smart fridge sending you a notification when you're out of milk or your fitness tracker syncing data to your phone. Cool stuff, right?
But here’s the kicker: all these devices need to communicate over the internet, and that’s where things can get tricky. When you slap a firewall on your network, it can sometimes block these communications, leaving your IoT devices stranded. So, how do we fix that?
Key Features of IoT
- Connectivity: IoT devices are always online, constantly exchanging data.
- Interactivity: These devices interact with users and other devices seamlessly.
- Automation: Many IoT systems operate automatically, reducing human intervention.
Firewall Basics: Why They Matter
A firewall is like a digital gatekeeper, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. It’s there to protect your network from unauthorized access and potential threats. But when it comes to IoT, firewalls can sometimes be a bit too overprotective.
Imagine trying to access your smart thermostat from your phone while you’re at work. If your firewall isn’t configured correctly, it might block that connection, leaving you stuck with a chilly house. That’s why understanding firewall basics is key to managing IoT devices effectively.
Types of Firewalls
- Packet Filtering Firewalls: Inspect individual packets of data.
- Stateful Inspection Firewalls: Track active connections and filter packets based on context.
- Application-Level Gateways: Analyze data at the application layer for more granular control.
Challenges of Controlling IoT Behind Firewalls
Controlling IoT devices behind a firewall comes with its own set of challenges. Firewalls are designed to block unauthorized access, which is great for security but not so great when you want your devices to communicate freely. Here are some common hurdles:
First off, IoT devices often use non-standard ports and protocols, which can confuse firewalls. Plus, with so many devices on a single network, managing all those connections can be a nightmare. And let’s not forget about potential vulnerabilities—IoT devices aren’t always the most secure, making them prime targets for hackers.
Read also:Alyx Star Date Of Birth Unveiling The Rise Of A Digital Sensation
Common Issues
- Blocked Connections: Firewalls may block legitimate IoT traffic.
- Configuration Complexity: Setting up firewalls for IoT can be tricky.
- Security Risks: Poorly configured firewalls can expose your network to attacks.
Solutions for Managing IoT Devices Securely
Luckily, there are solutions to help you manage IoT devices behind firewalls without sacrificing security. One approach is to use network segmentation, which involves dividing your network into smaller subnetworks. This way, you can isolate your IoT devices and apply specific firewall rules to them.
Another option is to leverage cloud-based IoT platforms that handle the heavy lifting for you. These platforms often come with built-in security features and can communicate with your devices through secure tunnels, bypassing firewall restrictions.
Effective Solutions
- Network Segmentation: Create separate zones for IoT devices.
- Cloud Platforms: Use cloud-based services for secure communication.
- Port Forwarding: Configure your firewall to allow specific ports for IoT traffic.
Top Tools to Control IoT Behind Firewalls
When it comes to managing IoT behind firewalls, having the right tools can make all the difference. Here are a few top picks:
First up, we’ve got UFW (Uncomplicated Firewall), a user-friendly firewall management tool for Linux. It’s perfect for setting up basic rules and keeping your IoT devices safe. Then there’s pfSense, a powerful open-source firewall that offers advanced features like VLAN support and intrusion detection.
Must-Have Tools
- UFW: Simple and effective for Linux users.
- pfSense: Advanced features for complex networks.
- Cloudflare: Secure DNS and firewall services for IoT.
Best Practices for IoT Security
Securing your IoT devices behind a firewall requires more than just setting up rules. You need to follow best practices to ensure your network stays safe. Start by updating your devices regularly—manufacturers often release patches to fix known vulnerabilities.
Next, use strong passwords and enable two-factor authentication wherever possible. And don’t forget to monitor your network for suspicious activity. Tools like Snort or Suricata can help you detect and respond to potential threats in real-time.
Top Tips for Security
- Regular Updates: Keep your devices and firmware up to date.
- Strong Authentication: Use complex passwords and 2FA.
- Network Monitoring: Keep an eye on your network for unusual behavior.
Designing a Robust Network Architecture
A well-designed network architecture is crucial for controlling IoT behind firewalls. Start by identifying your key devices and grouping them into logical categories. For example, you might have one group for home automation devices and another for security cameras.
Once you’ve organized your devices, set up VLANs (Virtual Local Area Networks) to further segment your network. This allows you to apply different firewall rules to each group, ensuring maximum security and functionality.
Architectural Elements
- VLANs: Create virtual networks for better segmentation.
- DMZ Zones: Isolate critical devices from the rest of your network.
- Load Balancers: Distribute traffic evenly across your devices.
Protecting Your Data in IoT Networks
Data protection is a top priority when it comes to IoT. With so many devices collecting and transmitting data, it’s essential to implement encryption and other security measures. Use protocols like HTTPS and TLS to encrypt data in transit, and store sensitive information in secure databases.
Additionally, consider implementing data anonymization techniques to protect user privacy. This involves removing or masking personally identifiable information from your data sets, making it harder for hackers to exploit.
Data Security Measures
- Encryption: Use HTTPS and TLS for secure communication.
- Anonymization: Protect user privacy by masking sensitive data.
- Access Control: Limit who can access your data.
Real-World Examples of IoT Behind Firewalls
Let’s look at some real-world examples of how organizations are successfully managing IoT behind firewalls. One company, a large manufacturing plant, uses industrial IoT devices to monitor production lines. By implementing network segmentation and advanced firewalls, they’ve been able to maintain security while still allowing devices to communicate freely.
Another example is a smart city initiative that uses IoT sensors to monitor traffic patterns. By leveraging cloud-based platforms and secure tunnels, they’ve managed to keep their network secure while providing valuable insights to city planners.
Future Trends in IoT and Firewall Management
The future of IoT and firewall management looks bright. As technology continues to evolve, we’re seeing more advanced solutions that make it easier to control IoT devices behind firewalls. One trend is the rise of AI-powered firewalls that can learn and adapt to new threats in real-time.
Another exciting development is the use of blockchain technology for secure IoT communication. By leveraging blockchain’s decentralized nature, devices can communicate directly with each other without relying on centralized servers, reducing the risk of single points of failure.
Emerging Technologies
- AI-Powered Firewalls: Adaptive learning for enhanced security.
- Blockchain: Decentralized communication for IoT devices.
- Edge Computing: Processing data closer to the source for faster response times.
Conclusion
Controlling IoT behind firewalls doesn’t have to be a headache. With the right tools, strategies, and best practices, you can ensure your devices stay secure while still functioning as intended. Remember to keep your network architecture robust, your data protected, and your firewall rules up to date.
So, what are you waiting for? Take control of your IoT network today and let us know how it goes. Drop a comment below or share this article with your tech-savvy friends. Together, let’s build a safer, smarter IoT world!