Unlock The Power Of SSH Device Over Internet: Your Ultimate Guide
Imagine this: You're chilling at home, sipping coffee, while controlling your work server from miles away. Sounds cool, right? Well, that’s where SSH device over internet comes in. Secure Shell (SSH) is like your secret weapon for remote device management. It’s not just about connecting; it’s about doing it safely. In today’s fast-paced world, having remote access to your devices is more than a luxury—it’s a necessity.
SSH device over internet is basically your golden ticket to accessing your computers, servers, or any network-enabled devices remotely. It’s like giving yourself a key to enter your digital world from anywhere. Whether you're troubleshooting a server issue or just grabbing a file you forgot, SSH has got your back. But hey, let’s not jump the gun here. There’s a lot more to it than meets the eye.
Now, before we dive deep into the nitty-gritty, let me tell you this: mastering SSH isn’t just about knowing the basics. It’s about understanding how to set it up securely, troubleshoot common problems, and explore the endless possibilities it offers. So, buckle up because we’re about to take you on a journey through the world of SSH. From setup tips to advanced configurations, we’ve got you covered.
Read also:Desi Indian 49 The Ultimate Guide To Understanding Her Impact And Journey
What is SSH Device Over Internet Anyway?
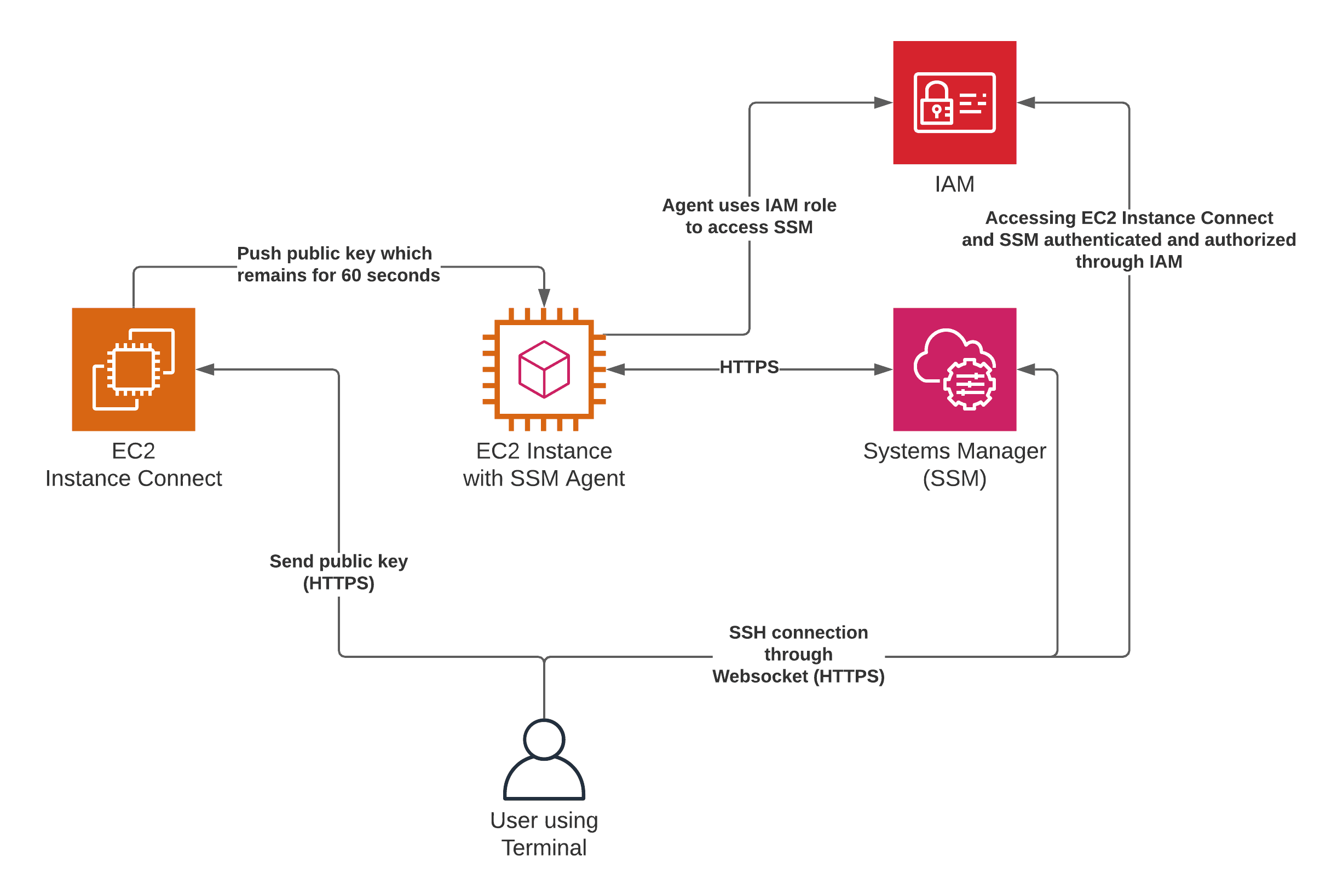
Okay, so let’s break it down. SSH, or Secure Shell, is a protocol that lets you connect to a device over the internet securely. Think of it as a secure tunnel that protects your data while it’s traveling between your computer and the device you’re accessing. Unlike other methods, SSH encrypts all your data, making it super hard for hackers to intercept.
When we talk about SSH device over internet, we’re referring to the ability to remotely control any SSH-enabled device from anywhere in the world. It’s not limited to just computers. You can SSH into servers, routers, IoT devices, and even some smart home gadgets. The possibilities are endless. But remember, with great power comes great responsibility. Security should always be your top priority when using SSH.
Why You Should Care About SSH Device Over Internet
Here’s the deal: SSH isn’t just for tech geeks or IT professionals. It’s for anyone who wants to have more control over their digital life. Whether you’re a small business owner managing a server or a college student accessing files from your dorm room, SSH can simplify your life. It saves you time, increases productivity, and gives you peace of mind knowing your data is secure.
But wait, there’s more. SSH isn’t just about accessing devices. It’s also about automating tasks, transferring files securely, and even setting up virtual private networks (VPNs). In short, it’s a versatile tool that can adapt to your needs. So, whether you’re a beginner or a pro, SSH has something to offer you.
Setting Up SSH Device Over Internet: Step by Step
Alright, let’s get practical. Setting up SSH device over internet isn’t as scary as it sounds. Here’s a step-by-step guide to get you started:
- Install an SSH client on your local machine. On Linux and macOS, you’re good to go since SSH is built-in. For Windows, you might want to use PuTTY or the new Windows Terminal.
- Make sure your target device has an SSH server installed and running. Most Linux distributions come with OpenSSH pre-installed, but you might need to enable it.
- Find the IP address of the device you want to connect to. If it’s on a local network, you can use its private IP. For remote access, you’ll need its public IP or a domain name.
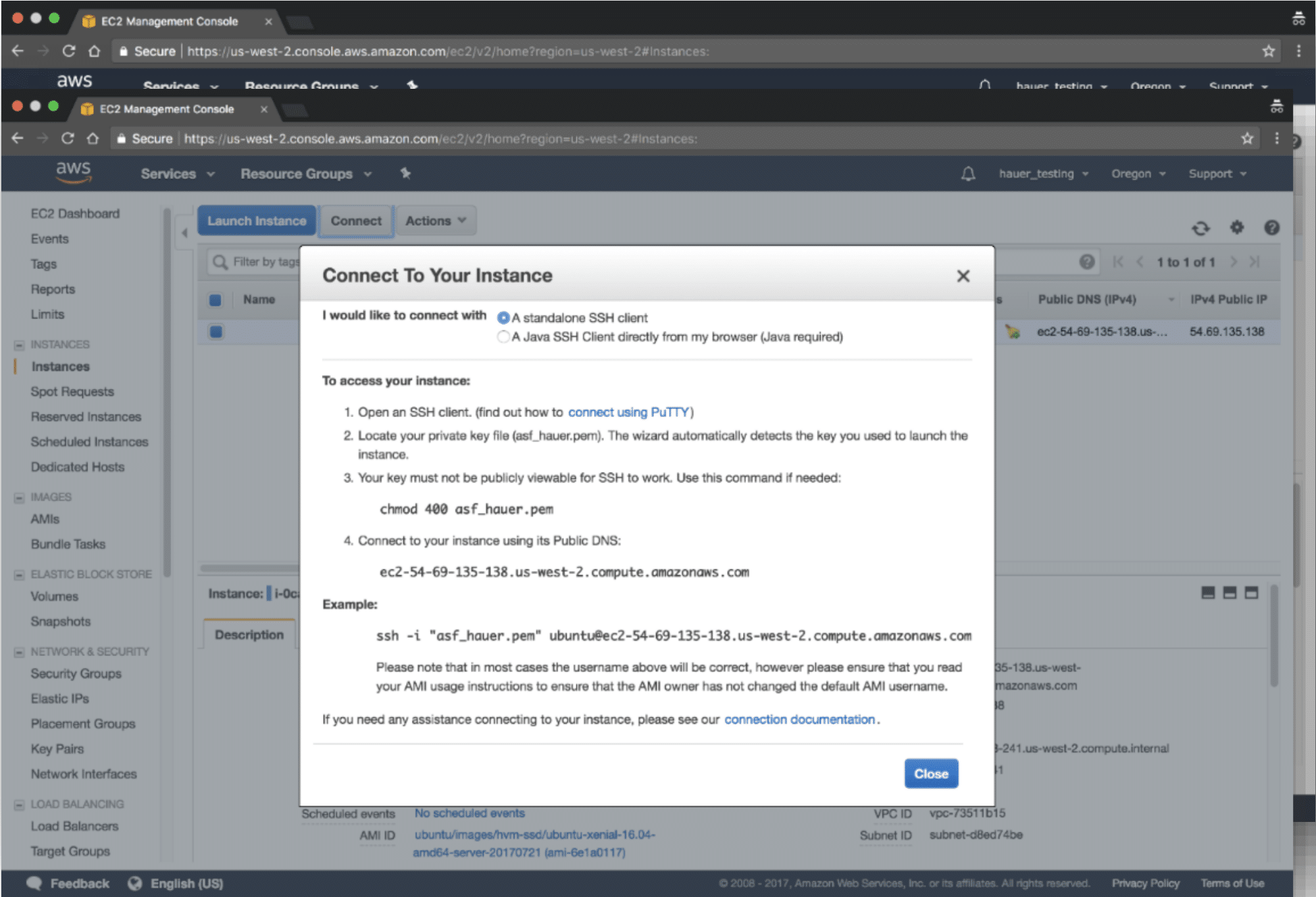
- Open your SSH client and enter the command: ssh username@ip_address. Replace "username" with the actual username and "ip_address" with the device’s IP.
- Enter the password when prompted, and voila! You’re in.
That’s it. You’re now connected to your device over the internet using SSH. Easy, right? But don’t forget to secure your setup. We’ll cover that in the next section.
Read also:Access Iot Behind Router Unlocking The Hidden Potential Of Your Smart Devices
Security Best Practices for SSH Device Over Internet
Security is the name of the game when it comes to SSH device over internet. Here are some tips to keep your connections safe:
- Use strong passwords: Avoid using simple or common passwords. Mix uppercase, lowercase, numbers, and symbols.
- Enable two-factor authentication (2FA): This adds an extra layer of security by requiring a second form of verification.
- Change the default SSH port: Instead of using the default port 22, switch to a higher, less common port to reduce automated attacks.
- Limit user access: Only allow specific users to connect via SSH. This minimizes the risk of unauthorized access.
- Regularly update your software: Keep your SSH client and server software up to date to protect against vulnerabilities.
By following these best practices, you can significantly reduce the risk of security breaches. Remember, prevention is always better than cure.
Common Issues and Troubleshooting
Even the best setups can have hiccups. Here are some common issues you might encounter when using SSH device over internet and how to fix them:
Connection Refused
This usually happens when the SSH server isn’t running or the port is blocked. Check if the SSH service is active and ensure that your firewall rules allow traffic on the SSH port.
Permission Denied
This error often occurs due to incorrect usernames or passwords. Double-check your credentials and make sure the user has the necessary permissions to log in via SSH.
Timeout Errors
If your connection keeps timing out, it might be due to network issues or a misconfigured SSH server. Try increasing the timeout settings or check your internet connection.
By addressing these issues promptly, you can ensure a smooth SSH experience. Don’t let small problems turn into big headaches.
Advanced SSH Features You Need to Know
Once you’ve mastered the basics, it’s time to level up your SSH game. Here are some advanced features you should explore:
- SSH Tunneling: Create secure tunnels to bypass firewalls or access restricted resources.
- SSH Keys: Ditch passwords and use SSH keys for more secure and convenient authentication.
- SSH Config File: Simplify your SSH commands by configuring common settings in the ~/.ssh/config file.
- SSHFS: Mount remote file systems securely using SSH.
These features can take your SSH skills to the next level. Don’t be afraid to experiment and find what works best for you.
SSH Device Over Internet: Use Cases and Applications
Now that you know how to set up and secure SSH, let’s talk about how you can use it in real-life scenarios:
Remote Server Management
Whether you’re running a website or hosting applications, SSH is your go-to tool for managing remote servers. You can install software, configure settings, and monitor performance from anywhere.
File Transfer
Need to move files between devices? SCP (Secure Copy Protocol) and SFTP (SSH File Transfer Protocol) are your best friends. They offer secure and reliable file transfers over SSH.
Automated Tasks
Set up scripts to automate routine tasks on your remote devices. From backups to system updates, SSH can handle it all.
With these use cases, you can see how versatile SSH is. It’s not just a tool; it’s a solution to many of your remote access needs.
SSH Device Over Internet: The Future of Remote Access
As technology continues to evolve, SSH will remain a cornerstone of secure remote access. Its adaptability and security features make it an indispensable tool for anyone working in a digital environment. Whether you’re managing servers, automating tasks, or simply accessing your files remotely, SSH has something to offer.
Looking ahead, we can expect even more advancements in SSH technology. From improved encryption methods to enhanced user interfaces, the future looks bright for SSH users. So, keep learning, experimenting, and exploring the possibilities.
Conclusion: Take Control of Your Digital World
We’ve covered a lot of ground today. From understanding what SSH device over internet is to mastering its setup and advanced features, you’re now equipped with the knowledge to take control of your digital world. Remember, security should always be your top priority. Follow the best practices we discussed, and you’ll be good to go.
So, what are you waiting for? Start using SSH today and see how it can transform the way you work. And don’t forget to share your SSH experiences in the comments below. Your feedback helps us improve and create more valuable content for you.
Table of Contents
- What is SSH Device Over Internet Anyway?
- Why You Should Care About SSH Device Over Internet
- Setting Up SSH Device Over Internet: Step by Step
- Security Best Practices for SSH Device Over Internet
- Common Issues and Troubleshooting
- Advanced SSH Features You Need to Know
- SSH Device Over Internet: Use Cases and Applications
- SSH Device Over Internet: The Future of Remote Access
- Conclusion: Take Control of Your Digital World