Mastering RemoteIoT Device SSH Tutorial: A Step-by-Step Guide For 2023
Alright, listen up, tech enthusiasts! If you're reading this, chances are you're diving headfirst into the world of IoT and remote device management. RemoteIoT devices are everywhere these days, and knowing how to securely access them is crucial. Whether you're a seasoned pro or just starting out, this remoteIoT device SSH tutorial is going to be your go-to guide. So, buckle up, because we're about to take you through everything you need to know to manage your IoT devices like a champ.
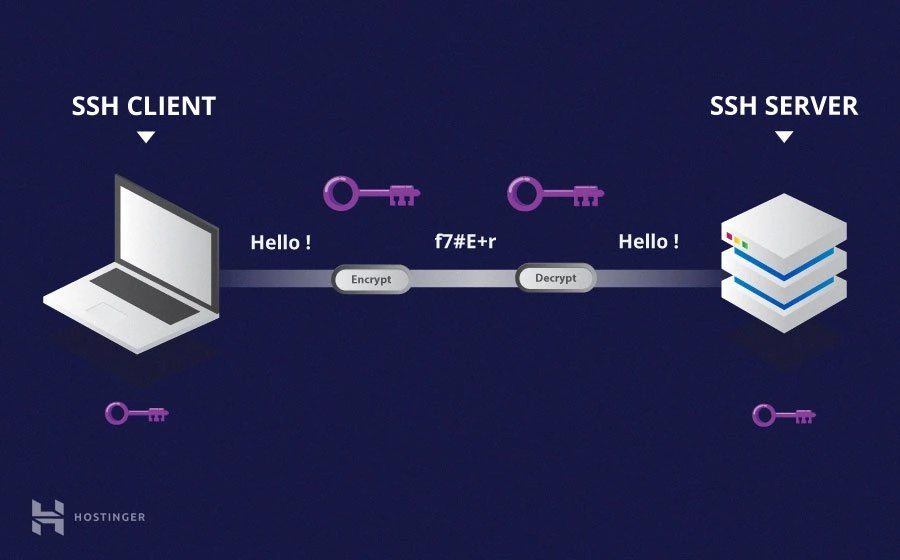
Now, before we dive deep into the nitty-gritty of remoteIoT device SSH, let me ask you something—do you know how critical secure access is when dealing with IoT devices? Imagine leaving your devices exposed to hackers or unauthorized access. It’s like leaving your front door wide open with a sign that says, "Come on in!" SSH (Secure Shell) is your digital lock and key, and understanding it will make your IoT setup more secure than Fort Knox.
But hold up! This isn’t just another boring tech article. We’re going to break it down in a way that’s easy to follow, practical, and full of real-world examples. So, whether you’re troubleshooting your home automation system or managing a fleet of industrial IoT devices, this tutorial will help you get the job done right.
Read also:New Tamilblasterscom Link Your Ultimate Guide To Accessing The Latest Movies
Why RemoteIoT Device SSH Matters
Let’s face it—IoT devices are everywhere, from smart fridges to industrial sensors. But the real magic happens when you can manage these devices remotely. That’s where SSH comes in. SSH allows you to securely connect to your remoteIoT devices over an encrypted channel, protecting your data from prying eyes.
But why does it matter? Well, here’s the deal: IoT devices often lack the robust security features of traditional computers. They’re small, lightweight, and sometimes deployed in remote locations. Without proper security measures, they’re vulnerable to attacks. SSH ensures that your commands and data remain private, even on public networks.
SSH: More Than Just Remote Access
SSH isn’t just about logging in to your remoteIoT devices. It’s a versatile tool that can do so much more:
- File Transfer: Use SCP or SFTP to securely transfer files to and from your IoT devices.
- Tunneling: Create secure tunnels for other applications to communicate over.
- Command Execution: Run commands on your devices from anywhere in the world.
- Authentication: Use public key authentication for added security.
So, as you can see, SSH is more than just a way to log in—it’s a comprehensive solution for managing your IoT devices securely.
Getting Started with RemoteIoT Device SSH
Before we dive into the tutorial, let’s make sure you’re all set up. Here’s what you’ll need:
- A remoteIoT device with SSH enabled.
- A computer with an SSH client installed (like PuTTY for Windows or the built-in terminal for macOS/Linux).
- A basic understanding of Linux commands (if your device runs on Linux).
Got everything? Great! Now, let’s get started.
Read also:Remoteiot Behind Router Unlocking The Future Of Smart Connectivity
Step 1: Enable SSH on Your RemoteIoT Device
First things first—your IoT device needs to have SSH enabled. Most modern IoT devices come with SSH pre-installed, but you might need to enable it manually. Here’s how:
If you’re using a Raspberry Pi, for example, you can enable SSH by running:
sudo raspi-config
Then, navigate to “Interfacing Options” and select “SSH.” Easy peasy, right?
Step 2: Connect to Your RemoteIoT Device
Now that SSH is enabled, it’s time to connect. Open your terminal or SSH client and type:
ssh username@device_ip_address
Replace username with your device’s username and device_ip_address with the actual IP address of your IoT device. You’ll be prompted to enter a password. Once you’re in, you’re ready to start managing your device.
Securing Your RemoteIoT Device SSH Connection
Alright, now that you’re connected, let’s talk about security. SSH is secure by default, but there are a few extra steps you can take to make it even more robust:
1. Use Public Key Authentication
Instead of relying on passwords, use public key authentication. Here’s how:
- Generate a key pair on your local machine:
ssh-keygen. - Copy the public key to your IoT device:
ssh-copy-id username@device_ip_address. - Disable password authentication in your SSH config file (
/etc/ssh/sshd_config):PasswordAuthentication no.
With public key authentication, even if someone gets your password, they won’t be able to access your device.
2. Change the Default SSH Port
Attackers often scan for devices running on the default SSH port (22). Change it to something less obvious. In your SSH config file, update:
Port 22 to Port 2222 (or any other number).
Don’t forget to update your firewall rules to allow traffic on the new port.
Troubleshooting Common SSH Issues
Even the best-laid plans can go awry sometimes. Here are some common SSH issues and how to fix them:
1. Connection Refused
If you get a "Connection refused" error, double-check the following:
- Your device’s IP address.
- That SSH is enabled on your device.
- Your firewall rules to ensure the SSH port is open.
2. Permission Denied (Public Key)
This usually happens if your public key isn’t correctly configured on the server. Make sure your public key is in the ~/.ssh/authorized_keys file on your IoT device.
Advanced SSH Techniques for RemoteIoT Devices
Once you’ve mastered the basics, it’s time to level up your SSH skills. Here are a few advanced techniques to try:
1. SSH Tunnels
Create a secure tunnel for other applications to communicate over. For example, you can tunnel HTTP traffic:
ssh -L 8080:localhost:80 username@device_ip_address
This forwards traffic from port 8080 on your local machine to port 80 on your IoT device.
2. SSH Jump Hosts
If your IoT device is behind a firewall, you can use a jump host to connect:
ssh -J jump_host_user@jump_host_ip username@device_ip_address
This allows you to securely access your device even if it’s not directly reachable.
Best Practices for Managing RemoteIoT Devices
Managing IoT devices remotely is a big responsibility. Here are some best practices to keep in mind:
- Regularly update your device’s firmware and SSH software.
- Monitor your SSH logs for suspicious activity.
- Use strong, unique passwords (or better yet, public key authentication).
- Limit SSH access to trusted IP addresses if possible.
Following these practices will help keep your IoT devices secure and running smoothly.
Real-World Applications of RemoteIoT Device SSH
So, how does all this apply in the real world? Here are a few examples:
1. Home Automation
Use SSH to manage your smart home devices, like thermostats or security cameras, from anywhere in the world.
2. Industrial IoT
SSH is crucial for managing fleets of industrial sensors and machines, ensuring they remain secure and operational.
3. Environmental Monitoring
Deploy IoT devices in remote locations to monitor environmental conditions, and use SSH to access and analyze the data.
Conclusion: Take Control of Your IoT Devices Today
And there you have it—your ultimate remoteIoT device SSH tutorial. From enabling SSH to advanced techniques like tunnels and jump hosts, you now have the tools you need to manage your IoT devices securely and efficiently.
So, what are you waiting for? Go ahead and start experimenting. And remember, if you find this tutorial helpful, don’t forget to share it with your fellow tech enthusiasts. Who knows? You might just be helping someone else secure their IoT setup too. Happy hacking!