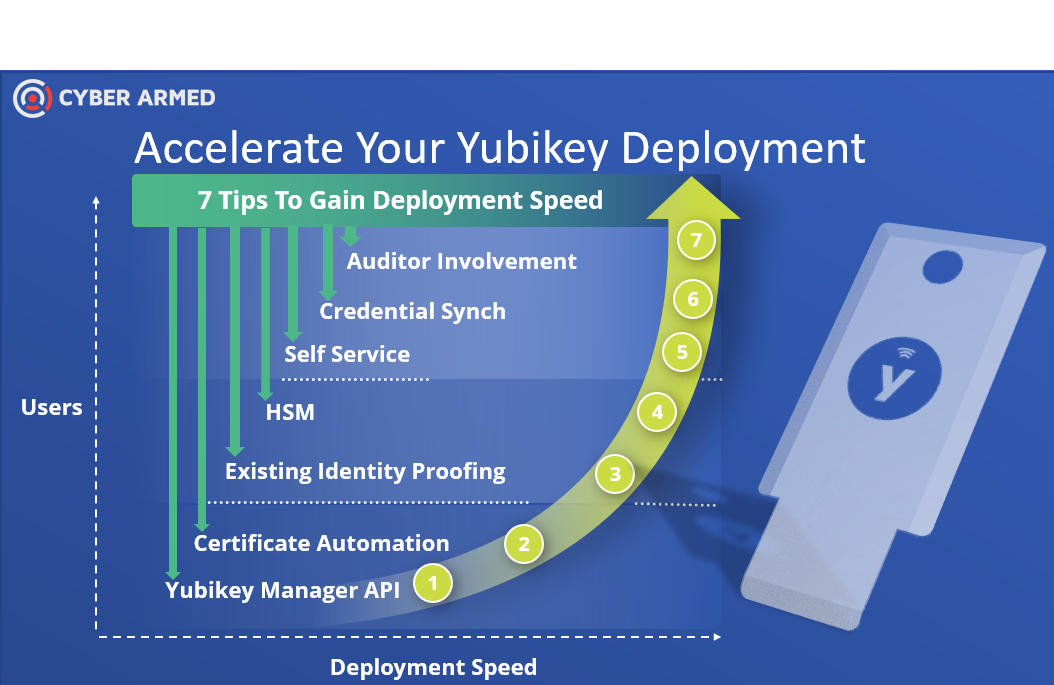
How To Deploy YubiKeys: The Ultimate Guide For Enhanced Security
Let’s face it, folks: security breaches are becoming more common than ever. And if you're not using a YubiKey by now, you're basically leaving your digital front door wide open. Deploying YubiKeys might sound intimidating at first, but trust me, it’s not as complicated as it seems. In this guide, we’ll break down everything you need to know about setting up and using YubiKeys to supercharge your cybersecurity game.
Now, you might be wondering, "What exactly is a YubiKey?" Great question! A YubiKey is a tiny hardware token that acts as your ultimate digital guardian. It provides top-notch authentication for your accounts, ensuring that only you—and no one else—can access your sensitive data. Whether you're protecting your email, cloud storage, or even your work accounts, YubiKeys are here to save the day.
But here’s the kicker: deploying YubiKeys isn’t just about plugging in a device. It’s about understanding how they work, setting them up properly, and integrating them into your daily routine. Don’t worry, though—we’ve got you covered. This article will walk you through every step of the process, from choosing the right YubiKey to troubleshooting common issues. Let’s dive in!
Read also:Lou Ferrigno The Incredible Hulk In Real Life
Why Deploy YubiKeys? Understanding the Importance of Hardware Authentication
Let’s cut to the chase: passwords are dead—or at least they should be. The average person has dozens of online accounts, and keeping track of strong, unique passwords for each one is a nightmare. That’s where YubiKeys come in. These little devices offer multi-factor authentication (MFA) that’s virtually impossible to hack.
Here’s why deploying YubiKeys is a game-changer:
- Increased Security: YubiKeys use cryptographic keys to verify your identity, making it nearly impossible for attackers to impersonate you.
- Convenience: No more remembering complex passwords or dealing with one-time codes sent via SMS. Just plug in your YubiKey and you’re good to go.
- Compatibility: YubiKeys work with a wide range of services, including Google, Microsoft, Dropbox, and more. They’re also compatible with both desktop and mobile devices.
So, if you’re tired of worrying about data breaches and want to take your security to the next level, deploying YubiKeys is the way to go. But before we dive into the nitty-gritty, let’s talk about how to choose the right YubiKey for your needs.
Choosing the Right YubiKey: A Beginner's Guide
Not all YubiKeys are created equal. Depending on your requirements, you’ll want to select a model that fits your specific use case. Here’s a quick rundown of the most popular YubiKey options:
YubiKey Nano: Compact and Convenient
If you’re looking for something small and portable, the YubiKey Nano is your best bet. It’s designed to stay inside your USB port, so you don’t have to worry about losing it. Plus, it supports both USB-A and USB-C connections, making it versatile for different devices.
YubiKey 5 Series: Feature-Rich and Versatile
The YubiKey 5 Series is the flagship model, offering a wide range of features, including FIDO2, U2F, and smart card functionality. If you need maximum security and flexibility, this is the YubiKey for you.
Read also:Attackertvtv Your Ultimate Streaming Destination For Actionpacked Entertainment
YubiKey Bio: Biometric Security at Its Finest
For those who want an extra layer of protection, the YubiKey Bio includes a fingerprint sensor for biometric authentication. It’s perfect for businesses or individuals who require top-tier security.
Now that you’ve got an idea of the different YubiKey models, let’s move on to the next step: setting up your YubiKey.
Setting Up Your YubiKey: Step-by-Step Guide
Setting up a YubiKey is surprisingly straightforward, but there are a few things you need to keep in mind. Follow these steps to get started:
Step 1: Purchase Your YubiKey
Head over to the official Yubico website or your preferred retailer to buy the YubiKey that suits your needs. Make sure you’re getting an authentic product to avoid any security risks.
Step 2: Register Your YubiKey
Once you’ve received your YubiKey, it’s time to register it. Visit the Yubico Personalization Tool website and follow the instructions to set up your device. This step is crucial, as it ensures that your YubiKey is properly configured for use.
Step 3: Configure MFA for Your Accounts
Now comes the fun part: enabling multi-factor authentication (MFA) for your accounts. Most major services, such as Google, Microsoft, and Dropbox, support YubiKey integration. Simply go to the security settings of each account, select “Add Security Key,” and follow the prompts to add your YubiKey.
And there you have it! Your YubiKey is now ready to protect your digital life. But wait, there’s more…
Best Practices for Deploying YubiKeys
Deploying YubiKeys isn’t just about setting them up—it’s about using them effectively. Here are some best practices to keep in mind:
- Use Strong Passwords: Even with a YubiKey, it’s important to use strong, unique passwords for your accounts. Think of the YubiKey as an added layer of protection, not a replacement for good password hygiene.
- Keep a Backup Key: Accidents happen, and you don’t want to get locked out of your accounts if you lose your primary YubiKey. Always keep a backup key in a safe place.
- Regularly Update Software: Make sure your operating system, browser, and any related software are up to date. This ensures that your YubiKey works seamlessly with all your devices.
By following these best practices, you’ll ensure that your YubiKey deployment is as secure and effective as possible. But what about troubleshooting? Let’s tackle that next.
Troubleshooting Common YubiKey Issues
Even the best-laid plans can go awry sometimes. If you’re having trouble with your YubiKey, here are some common issues and how to fix them:
Problem: YubiKey Not Detected
Solution: Make sure your device is properly plugged in and that your operating system supports the YubiKey’s connection type. Try restarting your device or using a different USB port.
Problem: MFA Not Working
Solution: Double-check that you’ve correctly added your YubiKey to the account’s security settings. If the issue persists, try resetting the YubiKey and re-registering it.
Problem: Lost or Damaged YubiKey
Solution: If you’ve lost or damaged your YubiKey, use your backup key to regain access to your accounts. Then, purchase a replacement key and update your account settings accordingly.
With these troubleshooting tips in mind, you’ll be able to resolve most YubiKey issues on your own. But if all else fails, don’t hesitate to reach out to Yubico support for assistance.
How to Deploy YubiKeys in Business Environments
Deploying YubiKeys isn’t just for individual users—it’s also a powerful tool for businesses looking to enhance their cybersecurity. Here’s how you can implement YubiKeys in a corporate setting:
Step 1: Assess Your Security Needs
Start by evaluating your organization’s security requirements. Identify which accounts and systems need the highest level of protection and prioritize deploying YubiKeys for those areas.
Step 2: Train Your Employees
Make sure your employees understand how to use YubiKeys effectively. Provide training sessions or resources to ensure everyone is on the same page.
Step 3: Monitor and Maintain
Regularly review your YubiKey deployment to ensure it’s functioning as intended. Address any issues promptly and update your policies as needed to stay ahead of potential threats.
By following these steps, you’ll create a secure and efficient YubiKey deployment strategy for your business.
The Future of YubiKeys: What’s Next?
As technology continues to evolve, so do the capabilities of YubiKeys. Here are a few trends to watch for in the future:
- Biometric Integration: Expect to see more YubiKeys with built-in biometric sensors, offering even greater levels of security.
- Expanded Compatibility: YubiKeys will likely become compatible with an even wider range of services and devices, making them even more versatile.
- Cloud-Based Authentication: The rise of cloud computing may lead to new ways of integrating YubiKeys with cloud-based security solutions.
The future of YubiKeys is bright, and it’s exciting to think about the possibilities that lie ahead. But for now, let’s focus on what we can do today to enhance our security.
Conclusion: Take Action and Secure Your Digital Life
Deploying YubiKeys might seem like a small step, but it’s a giant leap for your cybersecurity. By following the steps outlined in this guide, you’ll be well on your way to protecting your sensitive data from prying eyes.
So, what are you waiting for? Grab a YubiKey, set it up, and start enjoying the peace of mind that comes with knowing your accounts are secure. And don’t forget to share this article with your friends and family—because cybersecurity is everyone’s responsibility.
Have any questions or tips about deploying YubiKeys? Drop a comment below, and let’s keep the conversation going!
Table of Contents
- Why Deploy YubiKeys?
- Choosing the Right YubiKey
- Setting Up Your YubiKey
- Best Practices for Deploying YubiKeys
- Troubleshooting Common YubiKey Issues
- How to Deploy YubiKeys in Business Environments
- The Future of YubiKeys
- Conclusion