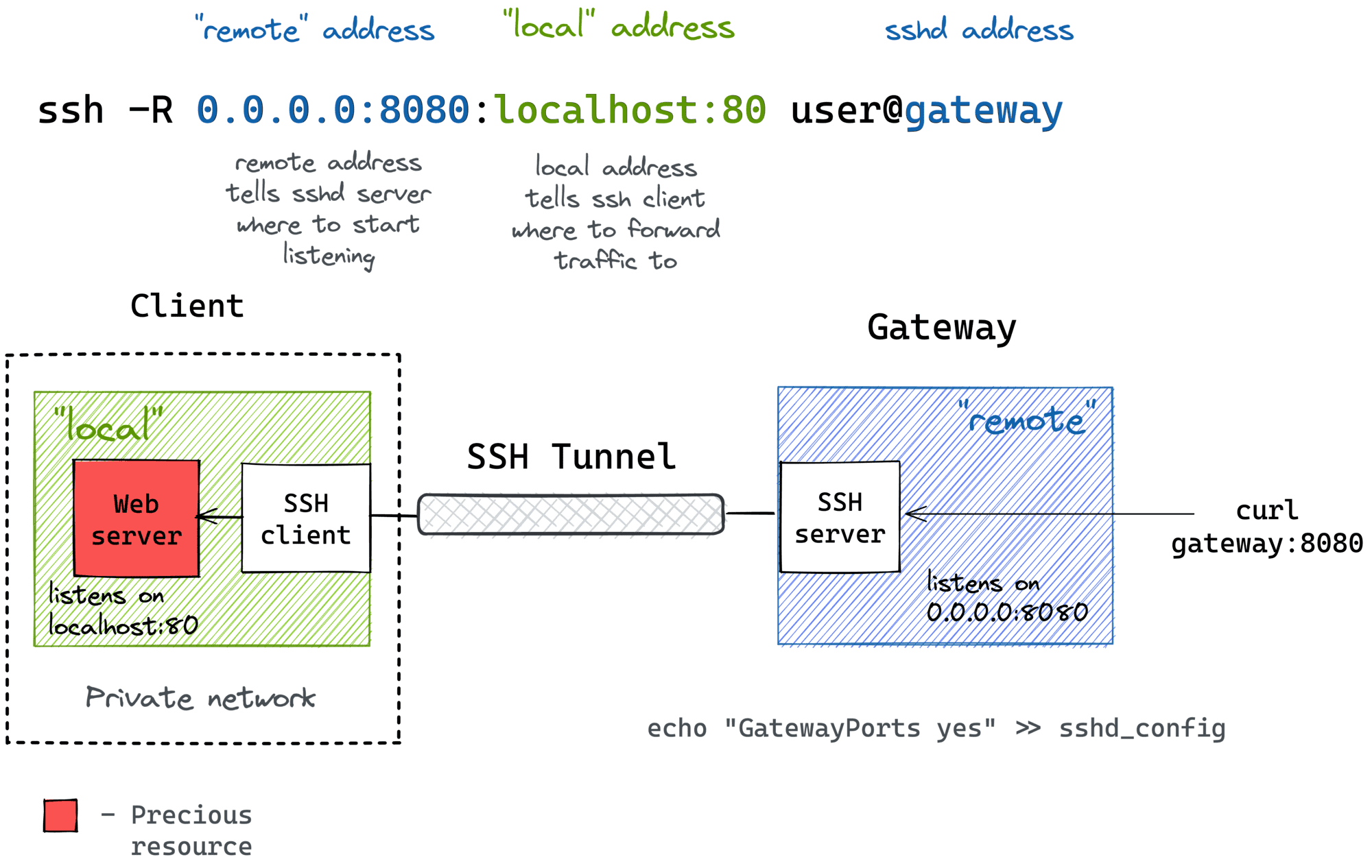
SSH Remote IoT Example: A Beginner's Guide To Securely Connecting Devices
Imagine this: you've got a bunch of IoT devices scattered across the globe, and you want to connect to them securely without exposing your network to hackers. That's where SSH remote IoT examples come into play. In today’s interconnected world, security is not just an option—it’s a must. Whether you’re managing home automation systems or industrial sensors, SSH provides the backbone for secure communication. But how exactly does it work? Let’s dive in and make sense of it all, step by step.
SSH, or Secure Shell, has been a go-to solution for secure communication for years. It’s like a digital Swiss Army knife for sysadmins, developers, and IoT enthusiasts alike. The beauty of SSH lies in its simplicity and robustness. You can establish encrypted connections, transfer files securely, and even execute commands remotely—all without worrying about prying eyes.
When it comes to IoT, SSH offers a way to manage devices remotely without compromising on security. Whether you're monitoring temperature sensors, controlling smart locks, or managing industrial equipment, SSH remote IoT examples can help you set up secure connections that keep your data safe. Let’s explore the ins and outs of this powerful tool.
Read also:Unlocking The Power Of Remoteiot Vpc Ssh Raspberry Pi Aws For Free Windows Downloads
Why SSH Matters in IoT
In the realm of IoT, security is everything. Devices are often deployed in remote locations, making physical access a challenge. SSH steps in as the knight in shining armor, providing secure access to these devices from anywhere in the world. But what makes SSH so special?
- Encryption: SSH encrypts all data transmitted between your device and the server, making it nearly impossible for hackers to intercept sensitive information.
- Authentication: SSH uses public-key cryptography to ensure that only authorized users can access your devices.
- Flexibility: SSH supports a wide range of commands and protocols, making it versatile enough for almost any IoT application.
For example, imagine you’re managing a network of weather sensors spread across a large area. With SSH, you can securely connect to each sensor, retrieve data, and update firmware—all without leaving your desk. This level of convenience and security is what makes SSH indispensable in the IoT ecosystem.
How SSH Works in IoT
At its core, SSH is a protocol that allows you to establish a secure connection between two devices. In the context of IoT, this typically involves connecting to a remote device using a terminal or command-line interface. Here’s a quick breakdown of how it works:
When you initiate an SSH connection, the client (your computer) sends a request to the server (the IoT device). The server responds by providing its public key, which the client uses to verify the server’s identity. Once the identity is confirmed, a secure channel is established using encryption algorithms like AES or ChaCha20.
Let’s say you’re working with a Raspberry Pi-based IoT project. By installing an SSH server on the Pi, you can connect to it from anywhere in the world using just a few simple commands. This makes it easy to manage your device remotely, whether you’re troubleshooting issues or updating software.
Setting Up SSH on IoT Devices
Configuring SSH on IoT devices is surprisingly straightforward. Most modern IoT platforms come with SSH support built-in, so all you need to do is enable it and configure the necessary settings. Here’s a step-by-step guide to get you started:
Read also:Unveiling The World Of Ullu Web Series Uncut Your Ultimate Guide
- Enable SSH: Depending on your device, you may need to enable SSH through a web interface, command-line, or configuration file.
- Generate Keys: Create a public-private key pair on your computer and copy the public key to the IoT device. This ensures that only your computer can access the device.
- Test the Connection: Use a terminal or SSH client to connect to your device and verify that everything is working as expected.
For instance, if you’re using a Linux-based IoT device, you can enable SSH by running the command sudo systemctl enable ssh. Once enabled, you can connect to the device using the command ssh username@device-ip.
SSH Remote IoT Example: A Practical Walkthrough
Now that we’ve covered the basics, let’s dive into a practical example of how to use SSH in an IoT project. Imagine you’re building a smart home system with a Raspberry Pi as the central hub. Here’s how you can set up SSH to manage your system remotely:
Step 1: Install SSH Server
First, you’ll need to install an SSH server on your Raspberry Pi. This can be done using the following command:
sudo apt-get install openssh-server
Once installed, you can enable SSH by running:
sudo systemctl enable ssh
Step 2: Generate Public-Private Keys
Next, generate a public-private key pair on your computer using the following command:
ssh-keygen -t rsa -b 4096
This will create a key pair in the .ssh directory. Copy the public key to your Raspberry Pi using the command:
ssh-copy-id username@raspberrypi
Step 3: Connect to the Device
Finally, connect to your Raspberry Pi using the command:
ssh username@raspberrypi
That’s it! You’re now connected to your IoT device securely over SSH.
Benefits of Using SSH for IoT
SSH offers a range of benefits that make it an ideal choice for IoT applications. Here are just a few:
- Security: SSH encrypts all data transmitted between your device and the server, protecting it from eavesdropping and tampering.
- Scalability: SSH can handle multiple connections simultaneously, making it suitable for large-scale IoT deployments.
- Flexibility: SSH supports a wide range of commands and protocols, allowing you to perform virtually any task remotely.
For example, if you’re managing a fleet of IoT devices, SSH allows you to automate tasks like firmware updates, data collection, and system monitoring. This saves time and reduces the risk of human error.
Common Challenges with SSH in IoT
While SSH is a powerful tool, it’s not without its challenges. Here are some common issues you might encounter when using SSH in IoT projects:
- Network Connectivity: IoT devices often operate in remote locations with limited or unstable internet connections. This can make it difficult to establish a reliable SSH connection.
- Resource Constraints: Many IoT devices have limited processing power and memory, which can impact the performance of SSH.
- Key Management: Managing public-private key pairs across multiple devices can be a logistical challenge, especially for large-scale deployments.
Despite these challenges, SSH remains one of the most reliable and secure ways to manage IoT devices remotely. With careful planning and proper configuration, you can overcome these obstacles and ensure smooth operation of your IoT network.
Best Practices for SSH in IoT
To get the most out of SSH in your IoT projects, here are some best practices to keep in mind:
- Use Strong Passwords: While public-key authentication is preferred, if you must use passwords, make sure they’re strong and unique.
- Disable Root Login: Restricting root access to your devices adds an extra layer of security and reduces the risk of unauthorized access.
- Regularly Update Software: Keeping your SSH server and client software up to date ensures that you’re protected against the latest security threats.
For example, if you’re managing a network of industrial sensors, disabling root login and requiring public-key authentication can significantly reduce the risk of unauthorized access. Additionally, setting up automated software updates can help ensure that your devices are always running the latest, most secure version of SSH.
SSH vs. Other IoT Protocols
While SSH is a popular choice for IoT applications, it’s not the only option available. Other protocols like MQTT, CoAP, and HTTPS also offer ways to communicate securely with IoT devices. So, how does SSH stack up against these alternatives?
SSH excels in scenarios where secure, interactive access to devices is required. It’s particularly well-suited for tasks like remote management, file transfer, and command execution. However, for lightweight, real-time communication, protocols like MQTT and CoAP may be more appropriate.
For instance, if you’re building a home automation system that requires frequent updates and real-time monitoring, MQTT might be a better choice than SSH. On the other hand, if you need to perform complex tasks like firmware updates or system diagnostics, SSH is the way to go.
Conclusion
In conclusion, SSH offers a powerful and secure way to manage IoT devices remotely. By following the steps outlined in this guide, you can set up SSH on your IoT devices and start managing them from anywhere in the world. Whether you’re building a smart home system or managing industrial sensors, SSH provides the tools you need to keep your network secure and operational.
So, what are you waiting for? Dive into the world of SSH remote IoT examples and take your IoT projects to the next level. And don’t forget to share your thoughts and experiences in the comments below. We’d love to hear how you’re using SSH in your projects!
Table of Contents
- Why SSH Matters in IoT
- How SSH Works in IoT
- Setting Up SSH on IoT Devices
- SSH Remote IoT Example: A Practical Walkthrough
- Benefits of Using SSH for IoT
- Common Challenges with SSH in IoT
- Best Practices for SSH in IoT
- SSH vs. Other IoT Protocols
- Conclusion